Encrption

Encryption
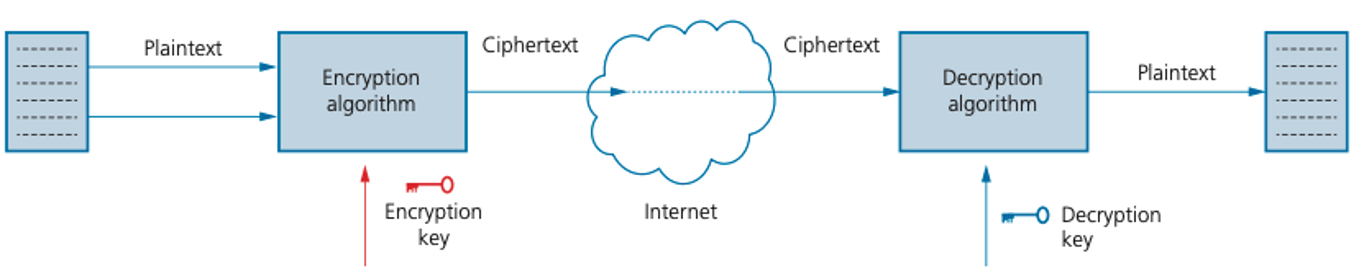
A hacker is often referred to as an eavesdropper. Using encryption helps to minimise this risk.
The original data being sent is known as plaintext. Once it has gone through an encryption algorithm, it produces ciphertext:
Symmetric encryption
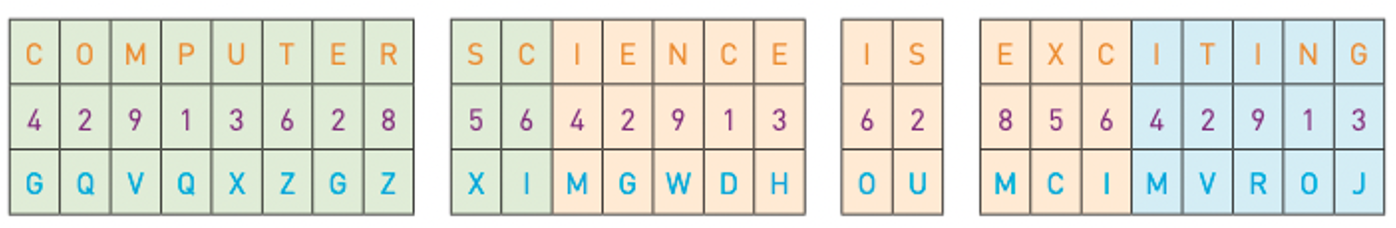
Symmetric encryption uses an encryption key; the same key is used to encrypt and decrypt the encoded message.
Suppose our encryption key is:
4 2 9 1 3 6 2 8 5 6
Asymmetric encryption
- Asymmetric encryption was developed to overcome the security problems associated with symmetric encryption.
- It makes use of two keys called the public key and the private key.
| Step | Process |
|---|---|
| 1 | 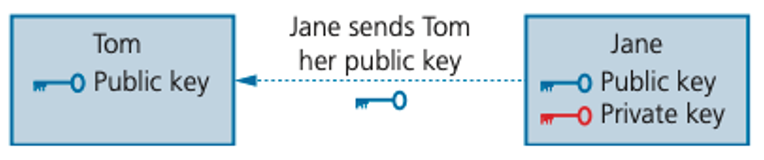 |
| 2 | Tom now uses Jane’s public key ( ) to encrypt the document he wishes to send to her |
| 3 | 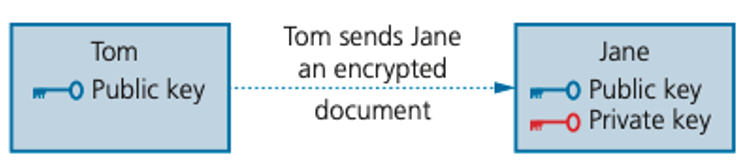 |
| 4 | Jane uses her matching private key ( ) to unlock Tom’s document and decrypt it |